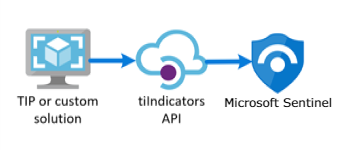
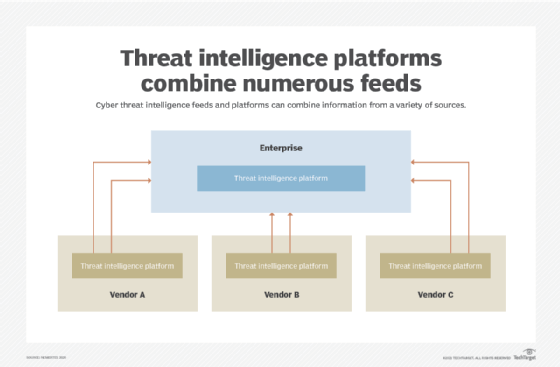
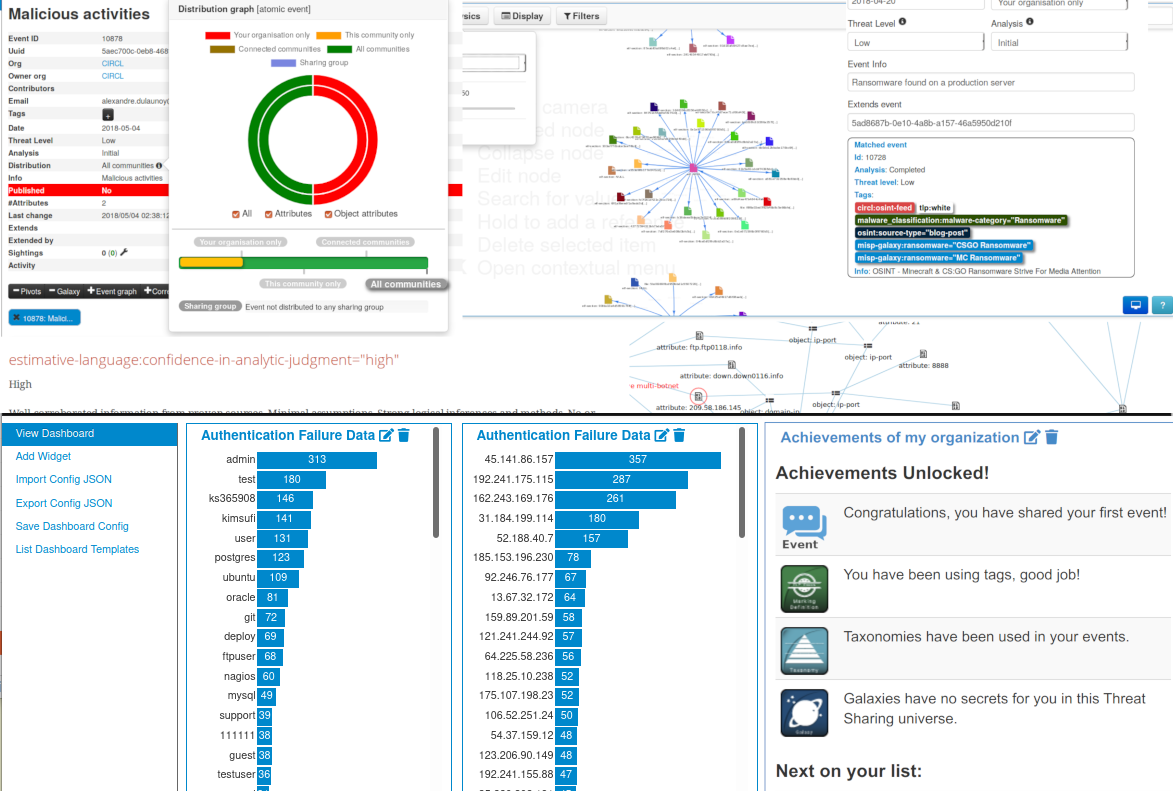
What Is Cyber Threat Intelligence? Definition, Objectives, Challenges, and Best Practices - Spiceworks

Full Cycle: Blending Intelligence Requirements and Custom Dissemination Tools to Drive Operations - YouTube
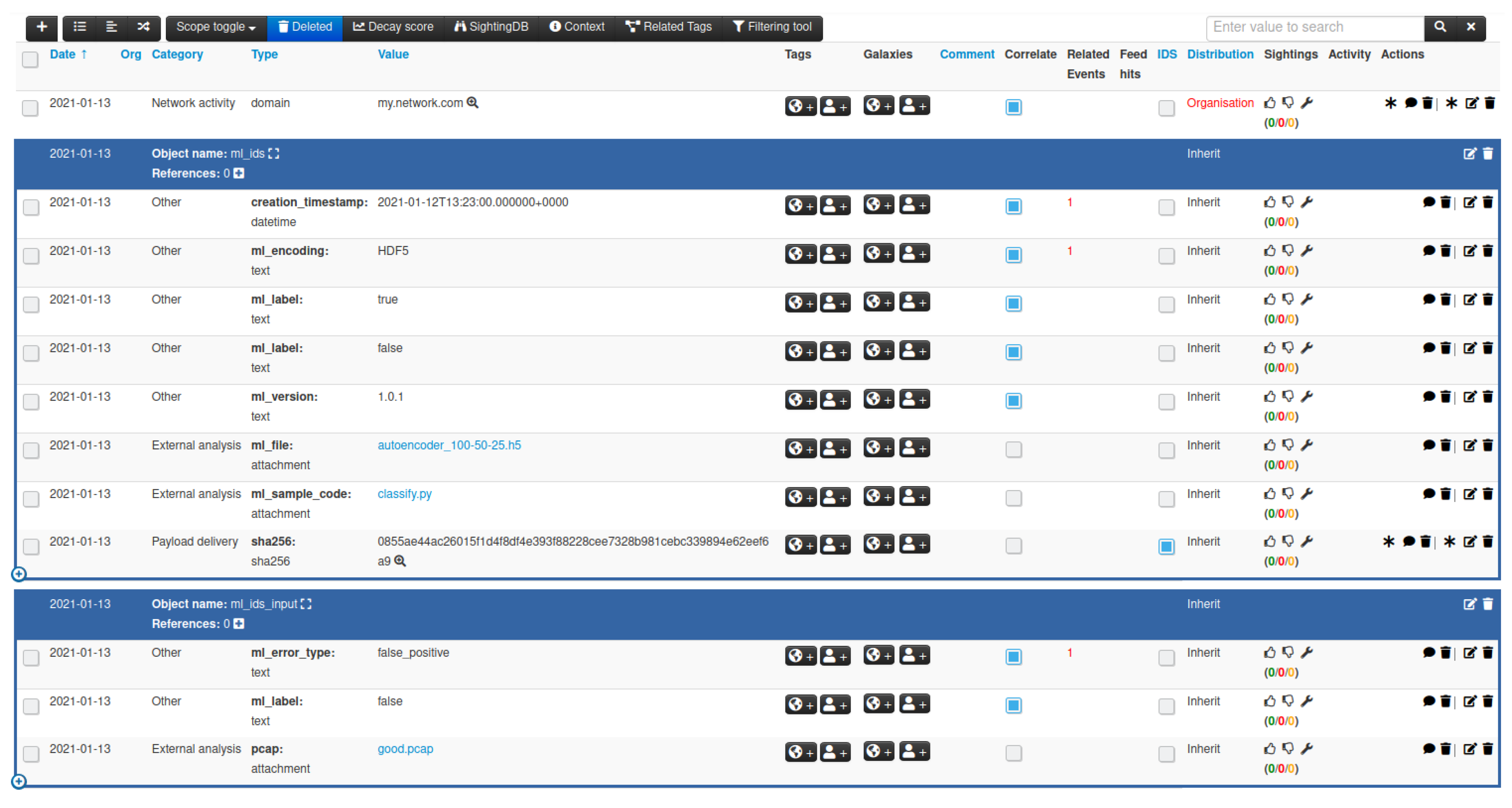
JCP | Free Full-Text | Sharing Machine Learning Models as Indicators of Compromise for Cyber Threat Intelligence

Full Cycle: Blending Intelligence Requirements and Custom Dissemination Tools to Drive Operations - YouTube