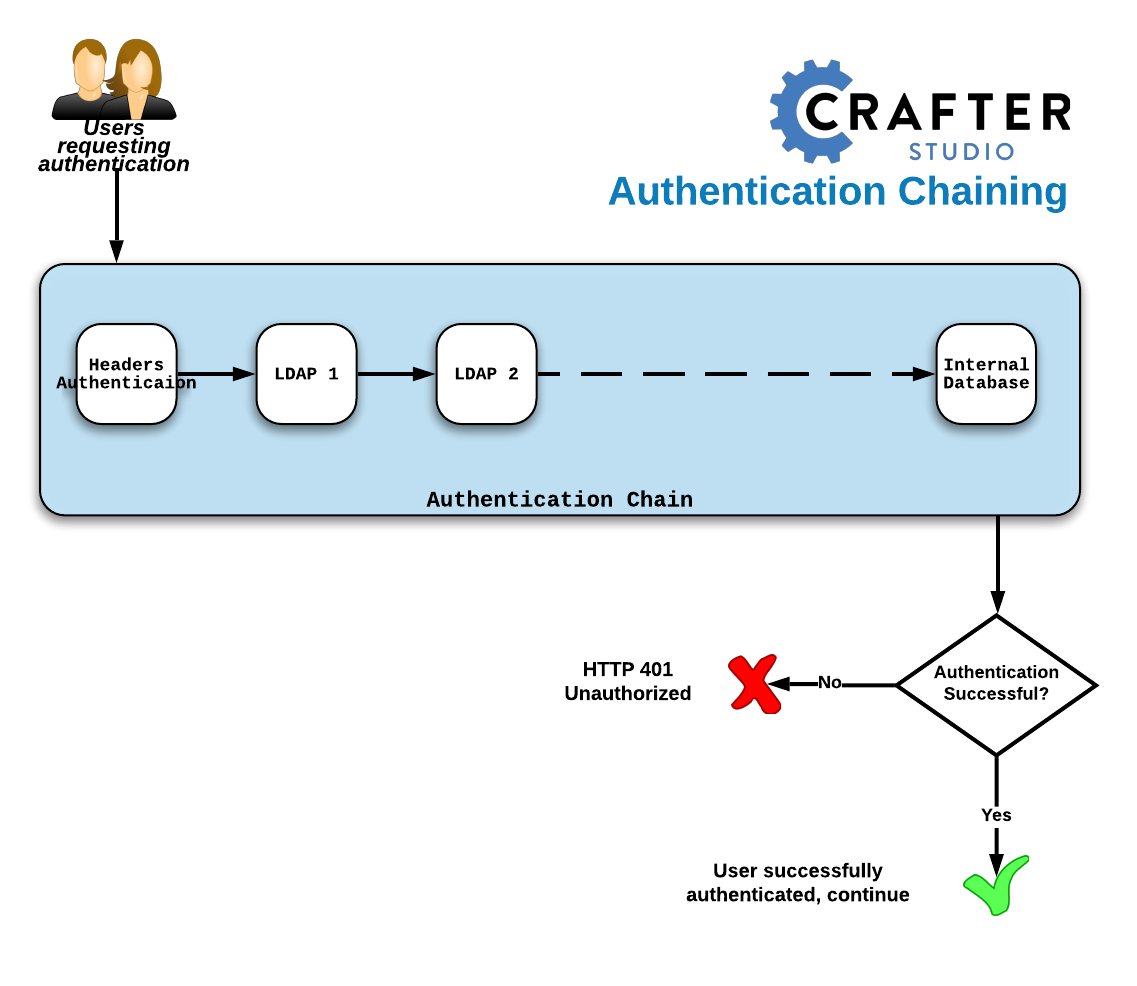
HELP.airflow datahub integration. Authentication chain failed to resolve a valid authentication · apache airflow · Discussion #26210 · GitHub
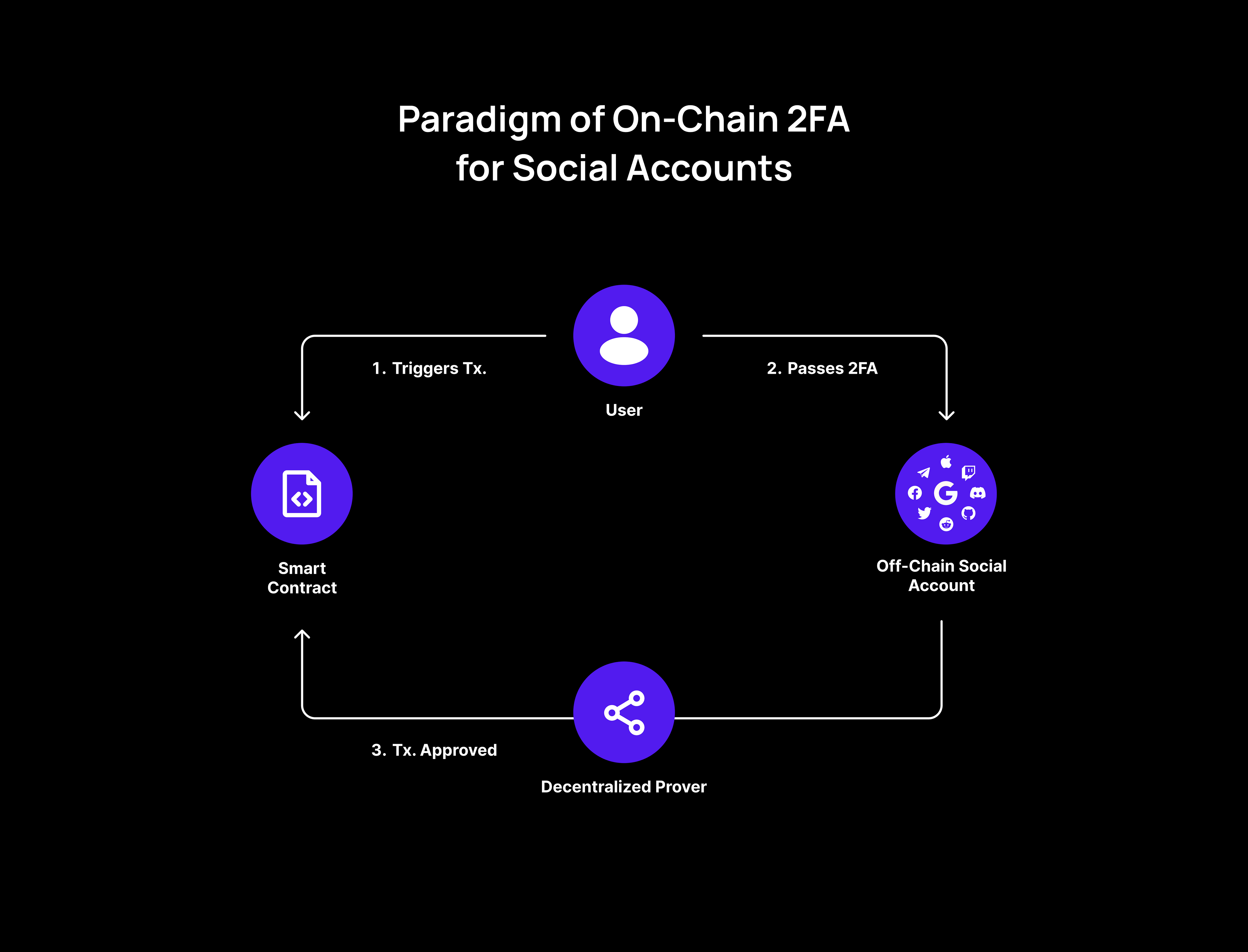
A Proposal of on-chain verifiable Social Identity 2 Factor Authentication - EIPs - Fellowship of Ethereum Magicians
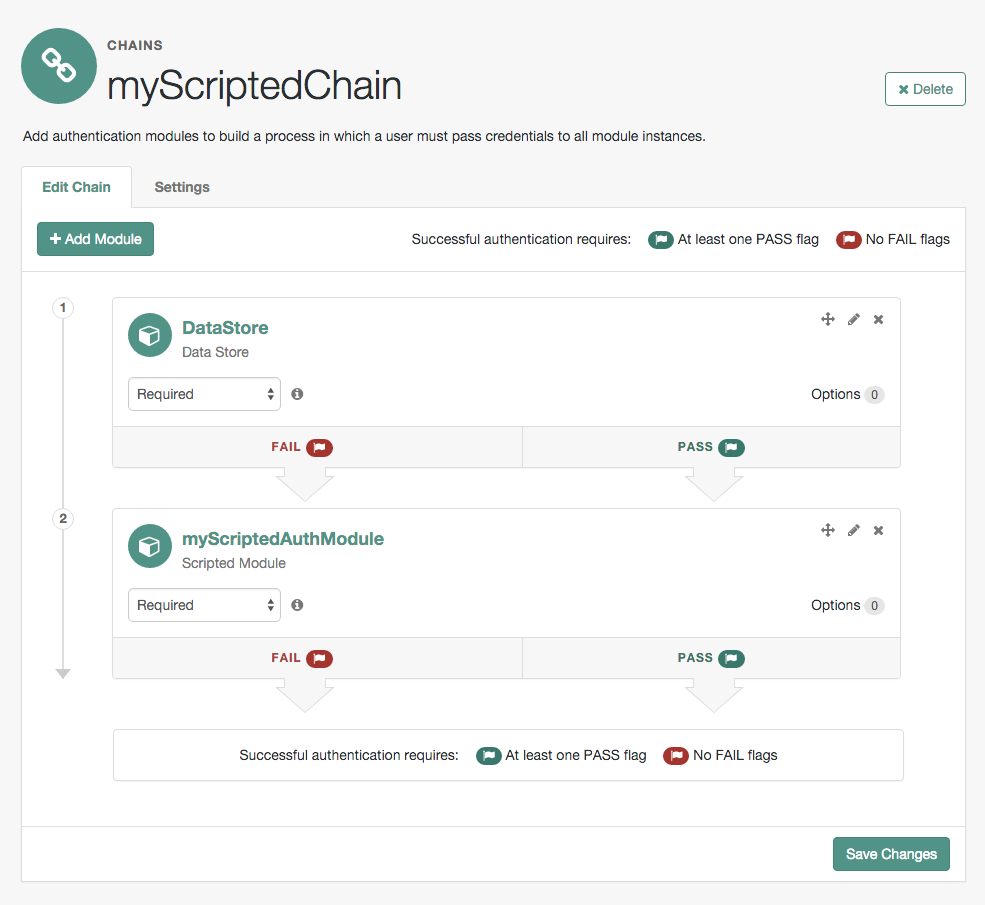
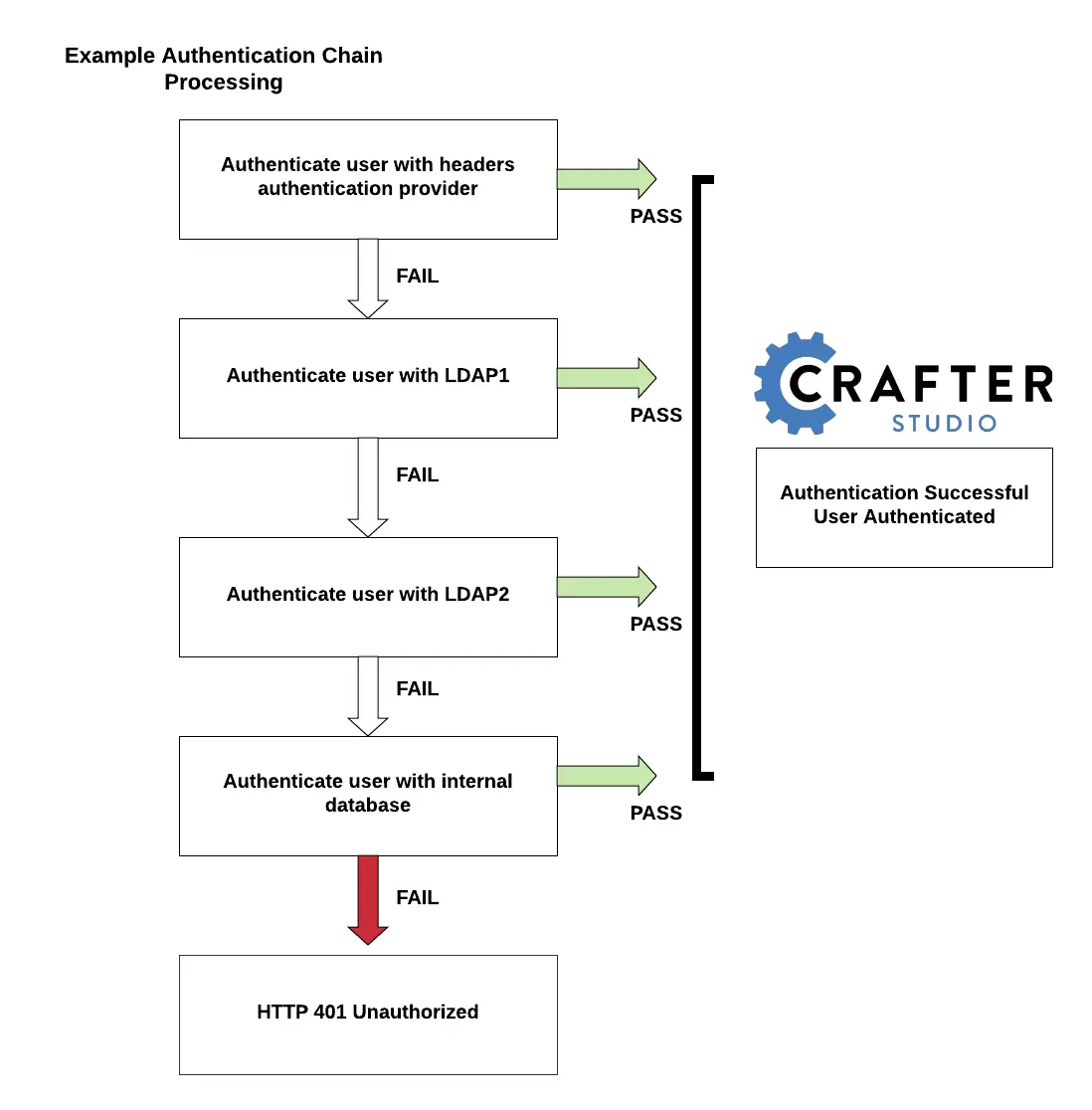
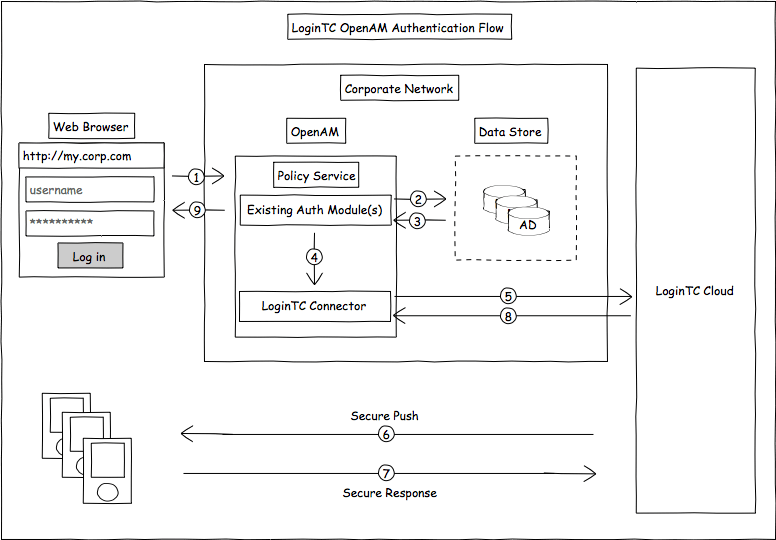
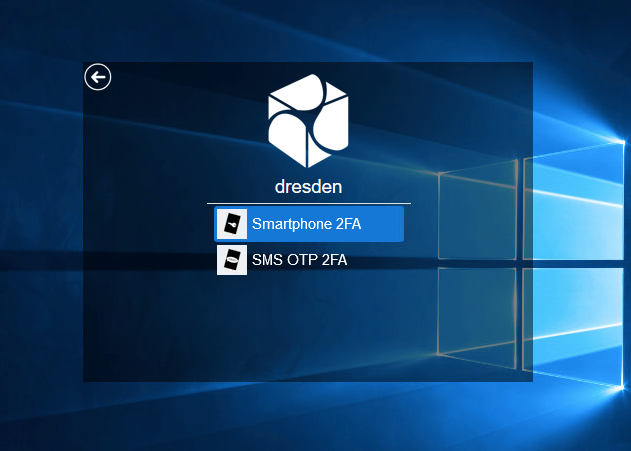
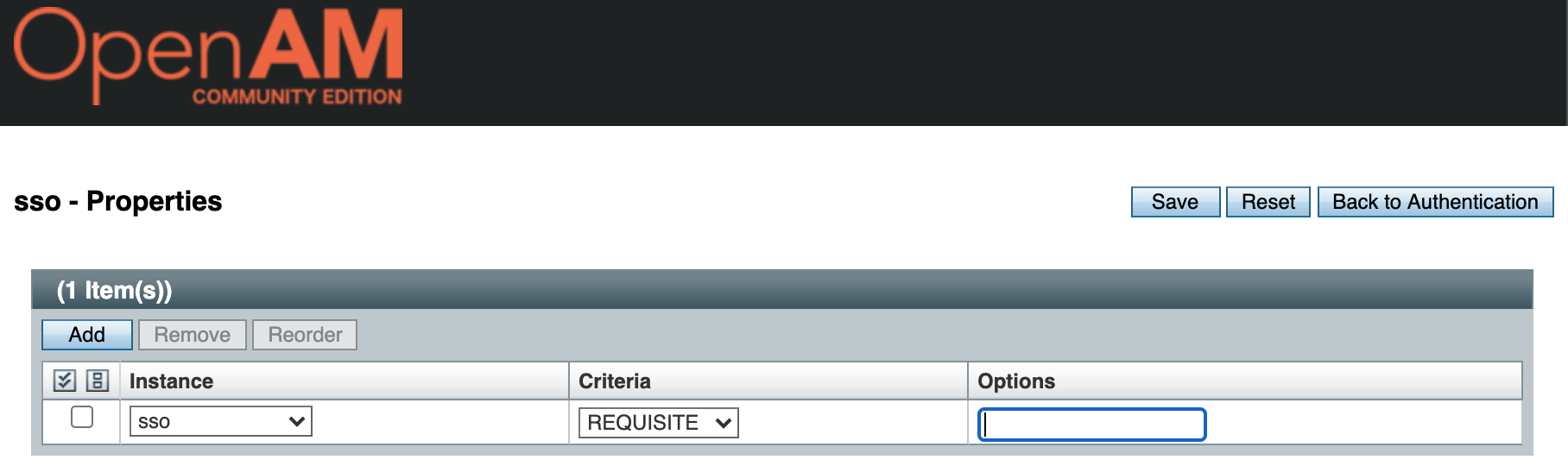
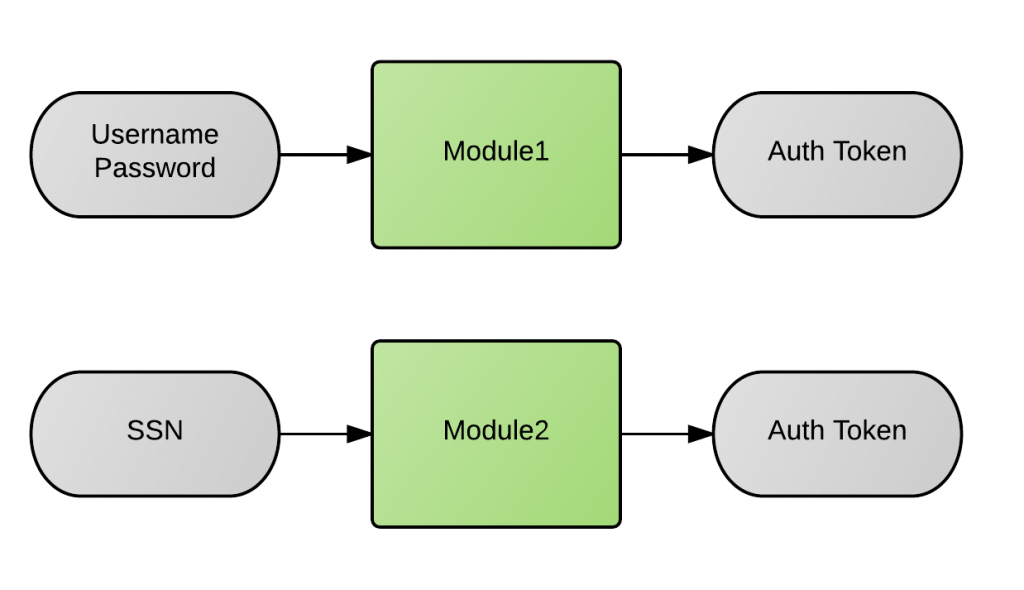
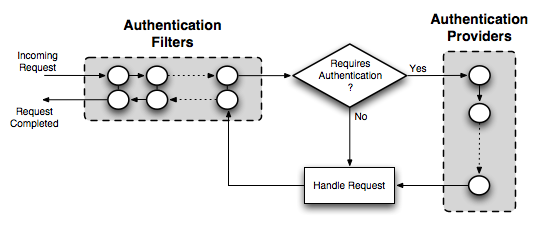
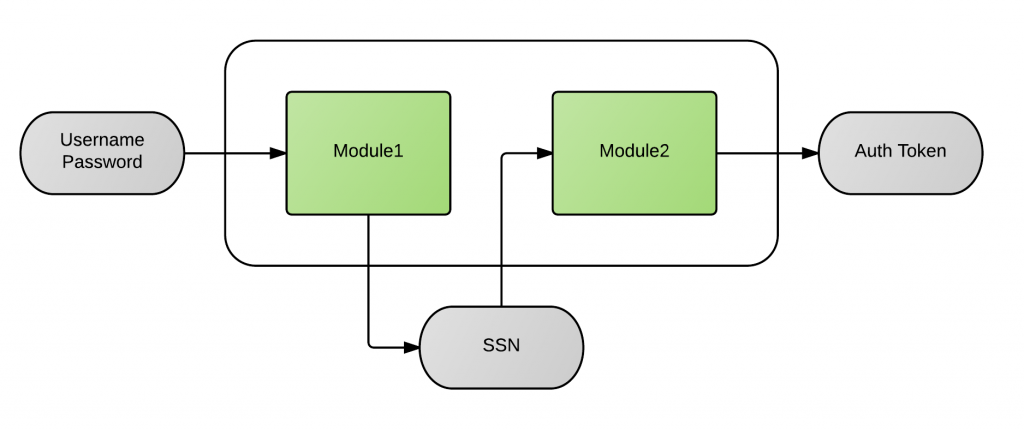
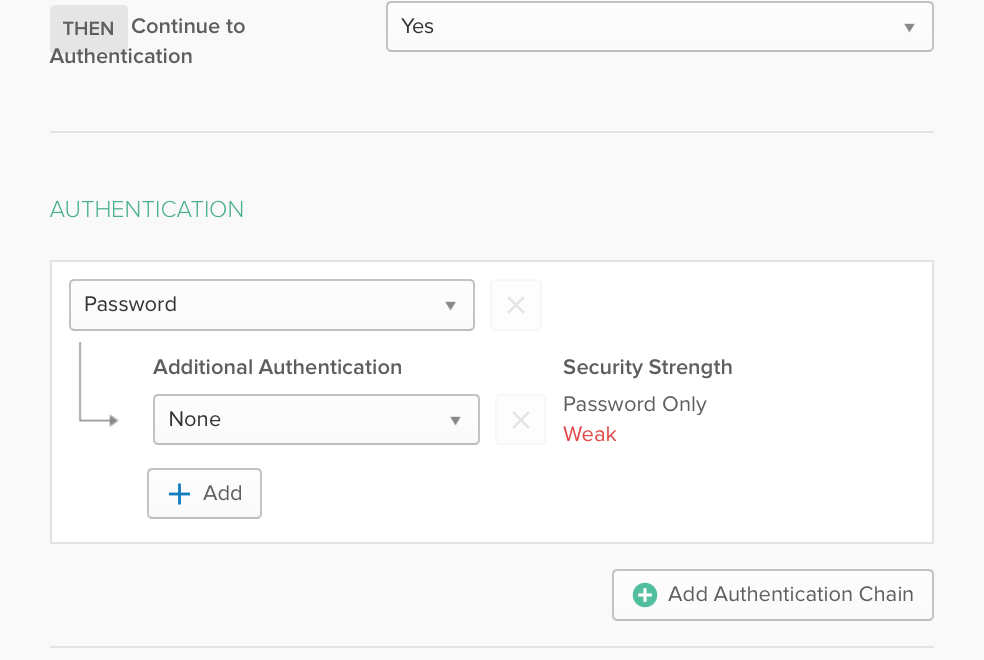
ForgeRock Access Management 7.0.2 > Authentication and Single Sign-On Guide > Authentication Modules and Chains

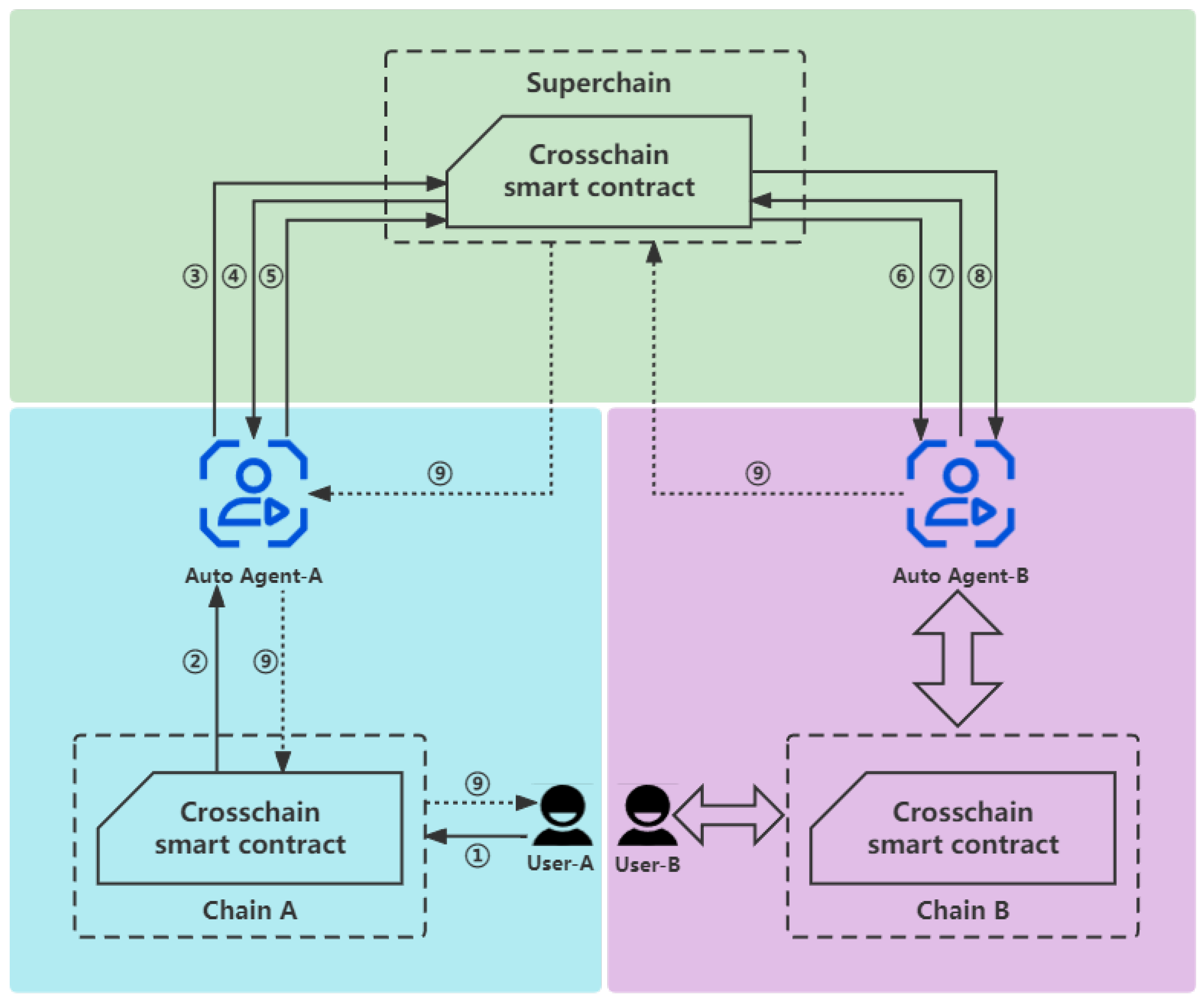
Mobile-Chain: Secure blockchain based decentralized authentication system for global roaming in mobility networks - ScienceDirect